If you haven’t set an AWS credential on your environment and EC2, you can’t call AWS API from the AWS CLI and SDK in your environment, computers or servers. In this article, I’ll cover how to set up a credential locally, how it works, and tested the precedence of credentials.
It’s also important how an IAM role works in EC2 with the credential. A temporary credentials for IAM role will be given to the running instance basically. As those credentials are delivered through the Amazon EC2 metadata service, it causes a problem sometimes, for example like this.
You can use the AWS CLI to call AWS API to control AWS resources, and most of of IaaS (Infrastucture as a service) AWS administration, management, and access functions by the AWS CLI are available. New AWS IaaS features and services provide full AWS Management Console functionality through the API and CLI at launch or within 180 days of launch. I think some minor operation and tricks could be executed by the AWS CLI only.
What is the AWS Command Line Interface?
Like mentioned in the above page, you’re usually navigated to use aws configure command to set up your configuration to use the AWS CLI. You can also issue this command to set up a credential in Linux and Windows EC2 instance if you’ve installed the AWS CLI software. Let’s have a look what happens by using this command at first.
$ aws configure
AWS Access Key ID [********************]:
AWS Secret Access Key [********************]:
Default region name [ap-northeast-1]: us-east-2
Default output format [None]: jsonThis commands creates a local file .aws/credentials and the stored credential is set to default profile. Now if you don’t specify any profile when you call the AWS API, the default profile is always taken. The command aws s3 ls and aws s3 ls –profile default are the same in this case. Let’s test this command.
$ aws s3 ls
2019-09-04 10:43:03 accesslog
$ aws s3 ls
--profile default
2019-09-04 10:43:03 accesslogThere is also a configuration file .aws/config created for the profile’s region and the output format. These attributes can be only overriden with the command line option. So basically the configuration files consist of .aws/credentials and .aws/config at your system’s home folder or directory.
It might have multiple profiles like below.
$ cat .aws/credentials
[default]
aws_access_key_id = *****
aws_secret_access_key = *****
[ecr]
aws_access_key_id = *****
aws_secret_access_key = *****
$ cat .aws/config
[default]
region = ap-northeast-1
output = None
[profile ecr]
region = ap-northeast-1
output = NoneHow to switch a profile for the AWS CLI?
I introduced one method to change a profile when you run a command. You can just give an option –profile in the command line. There is an alternative way by using the environment variable.
AWS_PROFILE is the environment variable you can set for your profile.
Configuration precedence
You might already know that environment variables are not used for only AWS_PROFILE but other credential information is also supported to pass. If you use command line options, the command line options take precedence over the environment variables. The credential information and options do not match, when only if equivalent parameter appears it’s overridden.
Here’s the precedence order for credential information.
- Command line option
- Environment variables
- Configuration files
- (IAM role, instance profile)
Command line option can control –region, –output and –profile related to credential. If you consider using the environment variables, you will not need to use those options in command line.
Configuration files .aws/credentials and .aws/config are next takers. Again these are the static files aws configure command creates. Please be careful you don’t have any environment variables overlapped with the configuration files.
How does an IAM role work for EC2?
The explanation of Using an IAM role in the AWS CLI might mislead the understanding a little. In this document, it looks a manual configuration in .aws/config to call role arn. Here’s the example to set an IAM role that is arn:aws:iam::123456789012:role/yourrole from instance’s metadata.
[profile yourrole]
role_arn = arn:aws:iam::123456789012:role/yourrole
credential_source = Ec2InstanceMetadatacredential_source = Ec2InstanceMetadata seems exactly the same effect of attaching to the Amazon EC2 instance profile. One benefit of this manual configuration is that you can select additional options such as the use of multi-factor authentication and an External ID (used by third-party companies to access their clients’ resources).
Here is the list of options we can pass to credential_source.

When you spin up an EC2 instance, the credential is empty first. So you can configure credential by command line or apply role arn manually in .aws/config with options.
$ aws configure list
Name Value Type Location
---- ----- ---- --------
profile <not set> None None
access_key <not set> None None
secret_key <not set> None None
region <not set> None NoneNow if we attached the IAM role to instance profile, the change of credential take effect immediately on the instance as below. Type changes to iam-role from shared-credentials-file.
If you issue aws configure command and generate .aws/credentials and .aws/config files, these files take precedence over instance profile and the result of aws configure list command will change.
$ aws configure list
Name Value Type Location
---- ----- ---- --------
profile <not set> None None
access_key ****************WDG7 iam-role
secret_key ****************YN83 iam-role
region <not set> None NoneIf your EC2 instance couldn’t obtain a temporary security credential from IAM role, the instance metadata service (IMDS) might not be accessible on the instance. You can confirm the documentation and access to the metadata service.
I can’t access the temporary security credentials on my EC2 instance
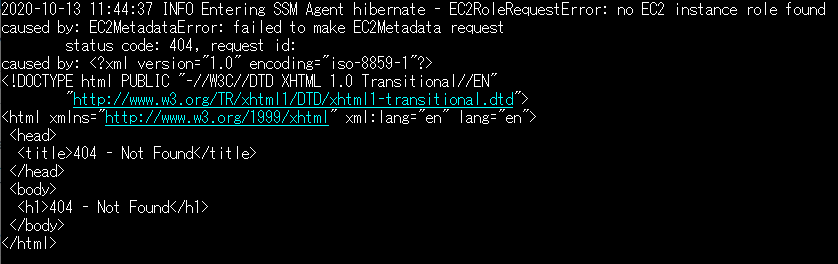
If you face an issue in Windows EC2 instance, it might be because of wrong netroutes as explained in this article.
How to fix “Unable to locate credentials” when execute AWS CLI on EC2 Windows Server?
To wrap up, there are multiple locations how to set up AWS credential for AWS resource accesses and precedences on those factors. It’s important to understand how AWS credential works in the AWS CLI and SDK, also for an instance profile when you use EC2 instance.
One thought on “How do AWS CLI credential and IAM role for EC2 work?”